Fortigate Vm License Crack
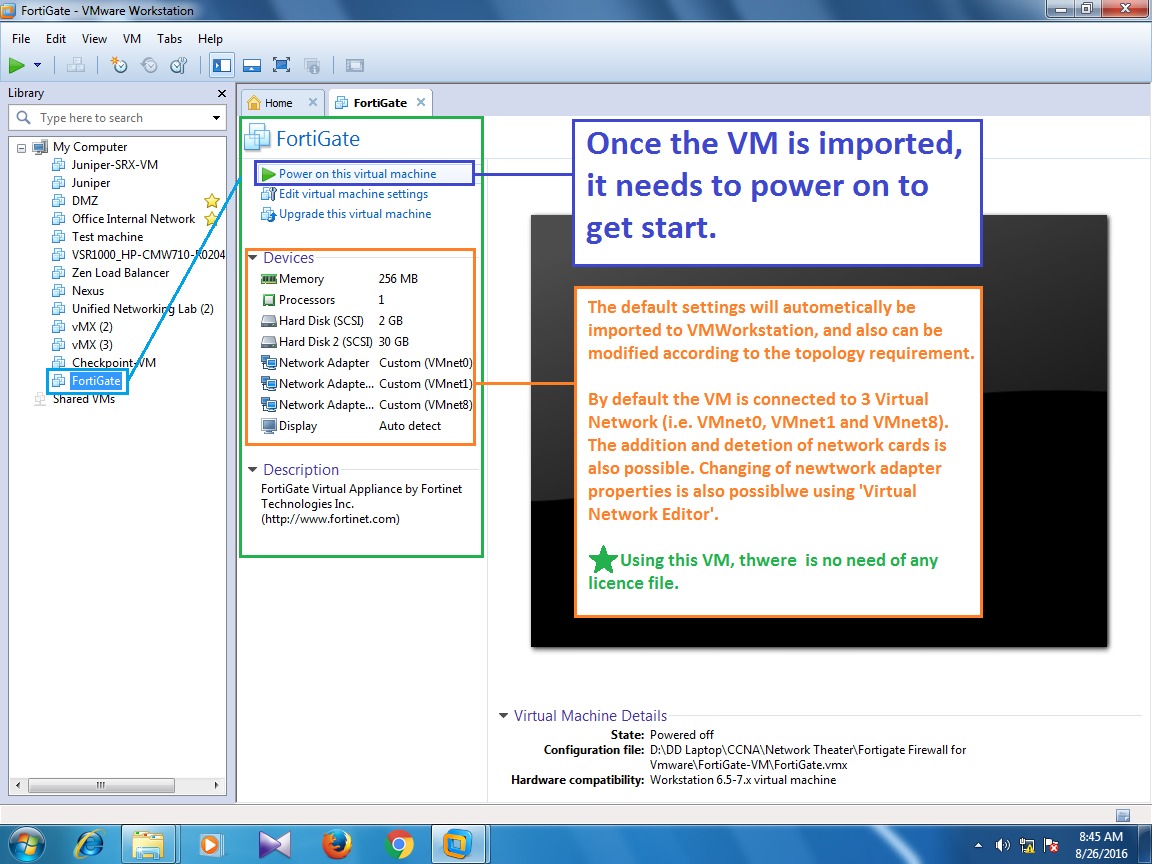
Integrating FortiOS (Fortigate VM64/VM32) into VMware. Here we will discuss on Fortigate (Fortigen Virtual FortiOS Apliance) Necessary downloads. Fortigate FortiOS VM Downlaod. After download, simply extract the file and open the fortigate.vmx file in VMware. Immediately after, it will be reflected on VMware window. Do not forget to change some initial setting before you fire up the Fortigate.

Home > Online Help
Validate the FortiGate VM license with FortiManager
You can validate your FortiGate VM license with some models of FortiManager. To determine whether your FortiManager unit has the VM Activation feature, see Features section of the FortiManager Product Data sheet.
To validate your FortiGate VM with your FortiManager:
- To configure your FortiManager as a closed network, enter the following CLI command on your FortiManager:
config fmupdate publicnetwork
set status disable
end
- To configure FortiGate VM to use FortiManager as its override server, enter the following CLI commands on your FortiGate VM:
config system central-management
set mode normal
set type fortimanager
set include-default-servers disable
set vdom <Enter the name of the VDOM to use when communicating with the FortiManager device>
config server-list
edit 1
set server-type update rating
set server-address <your FMG IP>
next
end
end
- Load the FortiGate VM license file in the Web-based Manager.
- Go to System > Dashboard > Status.
- In the License Information widget, in the Registration Status field, select Update. Browse for the
.liclicense file and select OK.
- To activate the FortiGate VM license, enter the following CLI command on your FortiGate VM:
execute update-now
- To check the FortiGate VM license status, enter the following CLI commands on your FortiGate VM:
get system status
The following output is displayed:
Version: Fortigate-VM v5.0,build0099,120910 (Interim)
Virus-DB: 15.00361(2011-08-24 17:17)
Extended DB: 15.00000(2011-08-24 17:09)
Extreme DB: 14.00000(2011-08-24 17:10)
IPS-DB: 3.00224(2011-10-28 16:39)
FortiClient application signature package: 1.456(2012-01-17 18:27)
Serial-Number: FGVM02Q105060000
License Status: Valid
BIOS version: 04000002
Log hard disk: Available
Hostname: Fortigate-VM
Operation Mode: NAT
Current virtual domain: root
Max number of virtual domains: 10
Virtual domains status: 1 in NAT mode, 0 in TP mode
Virtual domain configuration: disable
FIPS-CC mode: disable
Current HA mode: standalone
Distribution: International
Branch point: 511
Release Version Information: MR3 Patch 4
System time: Wed Jan 18 11:24:34 2012
diagnose hardware sysinfo vm full
The following output is displayed:
UUID: 564db33a29519f6b1025bf8539a41e92
valid: 1
status: 1
code: 200 (If the license is a duplicate, code 401 will be displayed)
warn: 0
copy: 0
Update Fortigate License
received: 45438
warning: 0
recv: 201201201918
dup:
Licensing timeout
In closed environments without Internet access, it is mandatory to perform offline licensing of the virtual FortiGate using a FortiManager as a license server. If the FortiGate-VM cannot perform license validation within the license timeout period, which is 30 days, the FortiGate will discard all packets and effectively ceasing operation as a firewall.
The status of the licence will go through some status changes before it times out.
| Status | Description |
|---|---|
| Valid | The FortiGate can connect and validate against a FortiManager or FDS |
| Warning | The FortiGate cannot connect and validate against a FortiManager or FDS. A check is made against how many days the Warning status has been continuous. If the number is less the 30 days the status does not change. |
| Invalid | The FortiGate cannot connect and validate against a FortiManager or FDS. A check is made against how many days the Warning status has been continuous. If the number is 30 days or more, the status changes to Invalid.The firewall ceases to function properly. |
| There is only a single log entry after the virtual FortiGate cannot access the license server for the license expiration period. This means that when you go searching the logs for a reason for the FortiGate being offline there will not be a long list of error logs that draw attention to the issue. There will only be the one entry. |
Copyright © 2018 Fortinet, Inc. All Rights Reserved. Terms of Service Privacy Policy
Anyone can Access FortiOS SSH Backdoor

Install Fortigate-vm License File
Proof-of-Concept Exploit Code is Available Online
Fortinet Response on the Issue
'This was not a 'backdoor' vulnerability issue but rather a management authentication issue. The issue was identified by our Product Security team as part of their regular review and testing efforts.'
